設定ファイルを含め、改竄対策として暗号化されているます。 そのため設定変更後は、専用コマンドで暗号化する必要があります。
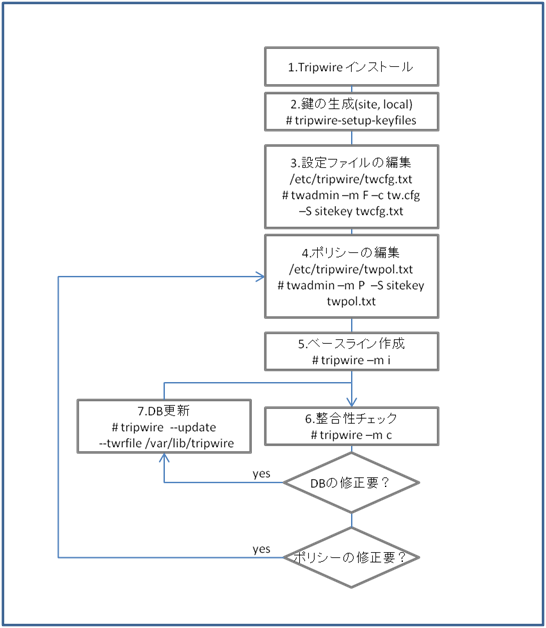
Tripwire はシステムセキュリティ上重要なファイルに関する情報を記録し、
定期定期にチェックすることで改竄を検知するツールです。
設定ファイルを含め、改竄対策として暗号化されているます。
そのため設定変更後は、専用コマンドで暗号化する必要があります。

# rpm -ivh /media/sf_share/tripwire-2.4.2.2-1.el5.i386.rpm Preparing... ########################################### [100%] 1:tripwire ########################################### [100%]
# tripwire-setup-keyfiles ---------------------------------------------- The Tripwire site and local passphrases are used to sign a variety of files, such as the configuration, policy, and database files. Passphrases should be at least 8 characters in length and contain both letters and numbers. See the Tripwire manual for more information. ---------------------------------------------- Creating key files... (When selecting a passphrase, keep in mind that good passphrases typically have upper and lower case letters, digits and punctuation marks, and are at least 8 characters in length.) Enter the site keyfile passphrase: Site パスフレーズ Verify the site keyfile passphrase: Site パスフレーズ Generating key (this may take several minutes)...Key generation complete. (When selecting a passphrase, keep in mind that good passphrases typically have upper and lower case letters, digits and punctuation marks, and are at least 8 characters in length.) Enter the local keyfile passphrase: Local パスフレーズ Verify the local keyfile passphrase: Local パスフレーズ Generating key (this may take several minutes)...Key generation complete. ---------------------------------------------- Signing configuration file... Please enter your site passphrase: Site パスフレーズ Wrote configuration file: /etc/tripwire/tw.cfg A clear-text version of the Tripwire configuration file: /etc/tripwire/twcfg.txt has been preserved for your inspection. It is recommended that you move this file to a secure location and/or encrypt it in place (using a tool such as GPG, for example) after you have examined it. ---------------------------------------------- Signing policy file... Please enter your site passphrase: Site パスフレーズ Wrote policy file: /etc/tripwire/tw.pol A clear-text version of the Tripwire policy file: /etc/tripwire/twpol.txt has been preserved for your inspection. This implements a minimal policy, intended only to test essential Tripwire functionality. You should edit the policy file to describe your system, and then use twadmin to generate a new signed copy of the Tripwire policy. Once you have a satisfactory Tripwire policy file, you should move the clear-text version to a secure location and/or encrypt it in place (using a tool such as GPG, for example). Now run "tripwire --init" to enter Database Initialization Mode. This reads the policy file, generates a database based on its contents, and then cryptographically signs the resulting database. Options can be entered on the command line to specify which policy, configuration, and key files are used to create the database. The filename for the database can be specified as well. If no options are specified, the default values from the current configuration file are used.
| パラメータ | 解説 | 推奨値 |
|---|---|---|
| LOOSEDIRECTORYCHECKING | ディレクトリ状態変化非検出(false) | true |
| MAILNOVIOLATIONS | エラー未検出のメール報告(true) | false |
| SMTPHOST | メールサーバ名、IP(なし) | localhost(追加) |
| SMTPPORT | メールサーバ名ポート(なし) | 25(追加) |
# cd /etc/tripwire # twadmin -m F -c tw.cfg -S site.key twcfg.txt Please enter your site passphrase: Site パスフレーズ Wrote configuration file: /etc/tripwire/tw.cfg
# twadmin -m P -S site.key twpol.new Please enter your site passphrase: Site パスフレーズ Wrote policy file: /etc/tripwire/tw.pol
# tripwire -m i Please enter your local passphrase: Local パスフレーズ Parsing policy file: /etc/tripwire/tw.pol Generating the database... *** Processing Unix File System *** Wrote database file: /var/lib/tripwire/vboxm.ycos.net.twd The database was successfully generated.
# cd /etc/tripwire/ # tripwire --init 2> tw.err Please enter your local passphrase: Local パスフレーズ Parsing policy file: /etc/tripwire/tw.pol Generating the database... *** Processing Unix File System *** Wrote database file: /var/lib/tripwire/vboxm.ycos.net.twd The database was successfully generated. # grep Filename tw.err | head -2 ### Filename: /dev/kmem ### Filename: /proc/ksyms # for f in `grep Filename tw.err |cut -d: -f2` > do > echo s, $f,#$f, > done > tw.sed # head -2 tw.sed s, /dev/kmem,#/dev/kmem, s, /proc/ksyms,#/proc/ksyms, # sed -f tw.sed twpol.txt > twpol.new # twadmin -m P -S site.key twpol.new Please enter your site passphrase: Site パスフレーズ Wrote policy file: /etc/tripwire/tw.pol # tripwire --init Please enter your local passphrase: Local パスフレーズ Parsing policy file: /etc/tripwire/tw.pol Generating the database... *** Processing Unix File System *** Wrote database file: /var/lib/tripwire/softbank219198124025.bbtec.net.twd The database was successfully generated.
# tripwire -m c
Parsing policy file: /etc/tripwire/tw.pol
*** Processing Unix File System ***
Performing integrity check...
Wrote report file: /var/lib/tripwire/report/vboxm.ycos.net-20120827-163424.twr
Open Source Tripwire(R) 2.4.2.2 Integrity Check Report
Report generated by: root
Report created on: Mon Aug 27 16:34:24 2012
Database last updated on: Mon Aug 27 09:49:14 2012
===============================================================================
Report Summary:
===============================================================================
Host name: vboxm.ycos.net
Host IP address: 192.168.151.4
Host ID: None
Policy file used: /etc/tripwire/tw.pol
Configuration file used: /etc/tripwire/tw.cfg
Database file used: /var/lib/tripwire/vboxm.ycos.net.twd
Command line used: tripwire -m c
===============================================================================
Rule Summary:
===============================================================================
-------------------------------------------------------------------------------
Section: Unix File System
-------------------------------------------------------------------------------
Rule Name Severity Level Added Removed Modified
--------- -------------- ----- ------- --------
Invariant Directories 66 0 0 0
Temporary directories 33 0 0 0
Tripwire Data Files 100 0 0 0
Critical devices 100 0 0 0
User binaries 66 0 0 0
Tripwire Binaries 100 0 0 0
Libraries 66 0 0 0
Operating System Utilities 100 0 0 0
Critical system boot files 100 0 0 0
File System and Disk Administraton Programs
100 0 0 0
Kernel Administration Programs 100 0 0 0
Networking Programs 100 0 0 0
System Administration Programs 100 0 0 0
Hardware and Device Control Programs
100 0 0 0
System Information Programs 100 0 0 0
Application Information Programs
100 0 0 0
(/sbin/rtmon)
Shell Related Programs 100 0 0 0
Critical Utility Sym-Links 100 0 0 0
Shell Binaries 100 0 0 0
* Critical configuration files 100 0 0 3
System boot changes 100 0 0 0
OS executables and libraries 100 0 0 0
Security Control 100 0 0 0
Login Scripts 100 0 0 0
* Root config files 100 2 0 3
Total objects scanned: 21085
Total violations found: 8
===============================================================================
Object Summary:
===============================================================================
-------------------------------------------------------------------------------
# Section: Unix File System
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Rule Name: Critical configuration files (/etc/hosts.allow)
Severity Level: 100
-------------------------------------------------------------------------------
Modified:
"/etc/hosts.allow"
-------------------------------------------------------------------------------
Rule Name: Critical configuration files (/etc/hosts.deny)
Severity Level: 100
-------------------------------------------------------------------------------
Modified:
"/etc/hosts.deny"
-------------------------------------------------------------------------------
Rule Name: Critical configuration files (/etc/hosts)
Severity Level: 100
-------------------------------------------------------------------------------
Modified:
"/etc/hosts"
-------------------------------------------------------------------------------
Rule Name: Root config files (/root)
Severity Level: 100
-------------------------------------------------------------------------------
Added:
"/root/bin"
"/root/bin/mycol"
Modified:
"/root"
"/root/.ssh/known_hosts"
-------------------------------------------------------------------------------
Rule Name: Root config files (/root/.bashrc)
Severity Level: 100
-------------------------------------------------------------------------------
Modified:
"/root/.bashrc"
===============================================================================
Error Report:
===============================================================================
No Errors
-------------------------------------------------------------------------------
*** End of report ***
Open Source Tripwire 2.4 Portions copyright 2000 Tripwire, Inc. Tripwire is a registered
trademark of Tripwire, Inc. This software comes with ABSOLUTELY NO WARRANTY;
for details use --version. This is free software which may be redistributed
or modified only under certain conditions; see COPYING for details.
All rights reserved.
Integrity check complete.
# export LANG=C # tripwire -m u --twrfile /var/lib/tripwire/report/vboxm.ycos.net-20120827-163424.twr ( vi が起動されレポートが表示される ) Please enter your local passphrase: Local パスフレーズ Wrote database file: /var/lib/tripwire/vboxm.ycos.net.twd(6)と(7)を同時に行う事も可能。
# export LANG=C # tripwire --check --interactive Parsing policy file: /etc/tripwire/tw.pol *** Processing Unix File System *** Performing integrity check... Wrote report file: /var/lib/tripwire/report/vboxm.ycos.net-20120827-094914.twr
| 機能 | コマンド |
|---|---|
| 設定ファイルの表示 | twadmin -m f twadmin --print-cfgfile |
| 設定ファイルの暗号化 | twadmin -m F -c tw.cfg -S site.key 設定ファイル twadmin --create-cfgfile -c tw.cfg -S site.key 設定ファイル |
| ポリシーファイルの表示 | twadmin -m p twadmin --print-polfile |
| ポリシーファイルの暗号化 | twadmin -m P -S site.key 設定ファイル twadmin --create-polfile -c tw.cfg -S site.key 設定ファイル |
| ベースラインの作成 | tripwire -m i tripwire --init |
| 整合性のチェック | tripwire -m c tripwire --check |
| DBの更新 | tripwire -m u -r レポートファイル tripwire --update --twrfile レポートファイル |
| テスト | tripwire -m t -e メアド tripwire --test --email メアド |
| DB情報表示 | trprint --print-dbfile |
| レポート表示 | trprint --print-report --twrfile レポートファイル |